We recently had a rogue network device brought from home and setup on our network. Typically its not a big deal. This person brought in a Sprint Airave which is to help with weak cell phone spots in your house. This device has its own built in DHCP server. So machines at one of our schools starting getting local address (192.168.x.x) and wouldn’t allow users to get out online.
Here are the steps we took to find it. We didn’t know what kind of device this was when we started fyi.
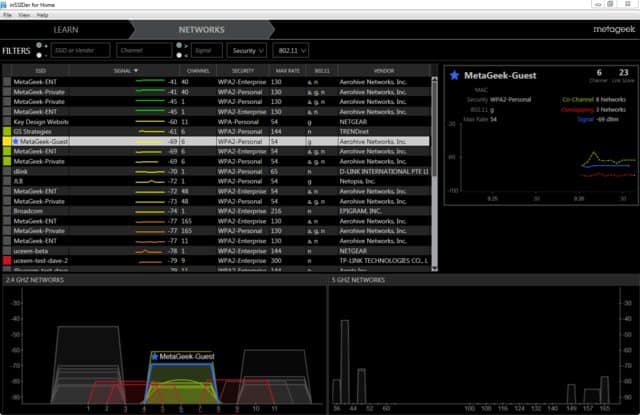
- Ran around the building using inSSIDer. Found some WiFi printers but that’s about it.
- We now knew it was a LAN device and not some wireless router.
- Ran Wireshark and noticed we had 192.168.x.x address spamming.
- Logged into the device by putting the default gateway address into the address bar. (typically the same numbers as the IP except the last number is 1)
- Disabled DHCP on the device and set an all staff email to ask who has the sprint device.
This is when I discovered how useful inSSIDer was. We used v3 and was susceptible to installing it after reading commands of it also installing bloatware. I never encountered any. Its easy to uncheck one box to say to the offer included with it.