LAPS provides a way to automatically rotate the local Administrator password on domain joined machines every X amount of days to a random password.
I’ll be installing it on one of my domain controllers.
Download LAPS and Install.
Download LAPS and be sure to install all the management tools also.
https://www.microsoft.com/en-us/download/details.aspx?id=46899
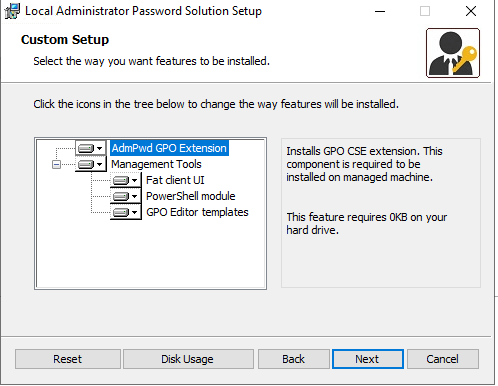
Extend the AD Schema
Open up PowerShell (run as admin) and run the following:
Import-module AdmPwd.PS
Update-AdmPwdADSchema
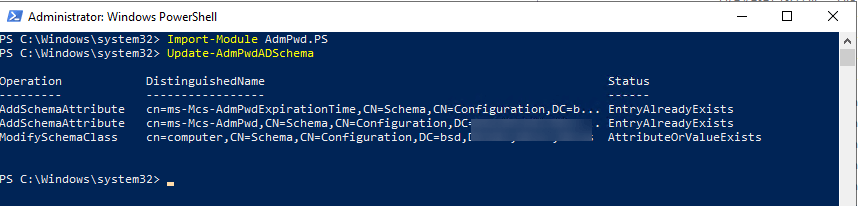
Provide AD Directory and Groups with permissions for read/reset
Set-AdmPwdComputerSelfPermission -OrgUnit "OU=YOURPATHHERE"
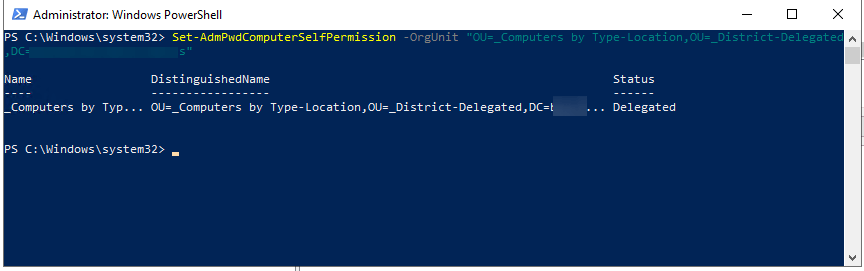
Now if you haven’t already create a security group that you’ll allow to change the local machine passwords. I’ve created one called LAPS.
Set-AdmPwdReadPasswordPermission -OrgUnit "OU=" -AllowedPrincipals "LAPS"
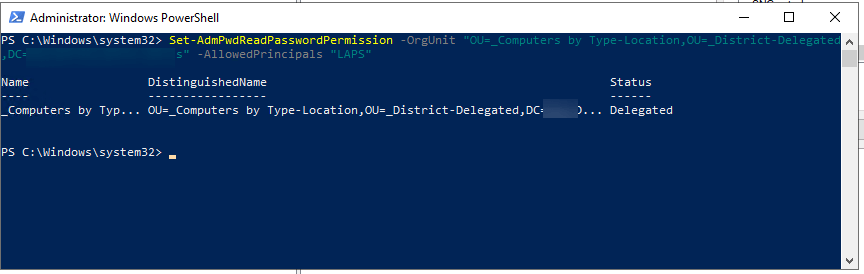
Now lets provide reset permission.
Set-AdmPwdResetPasswordPermission -OrgUnit "OU=" -AllowedPrincipals "LAPS"
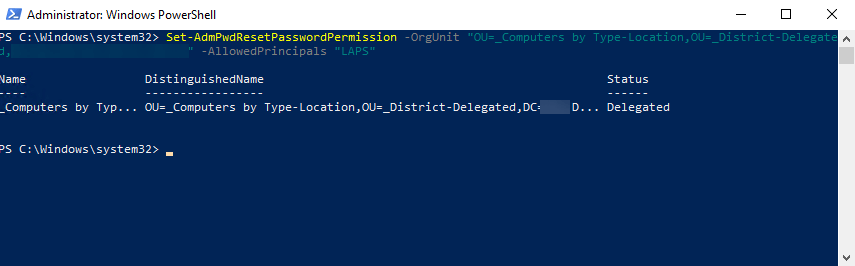
Create the Group Policy
Created your new GPO and deploy it to a test OU! Always make sure it works before deploying to production.
Expand Computer Configuration > Policies > Administrative Templates > LAPS
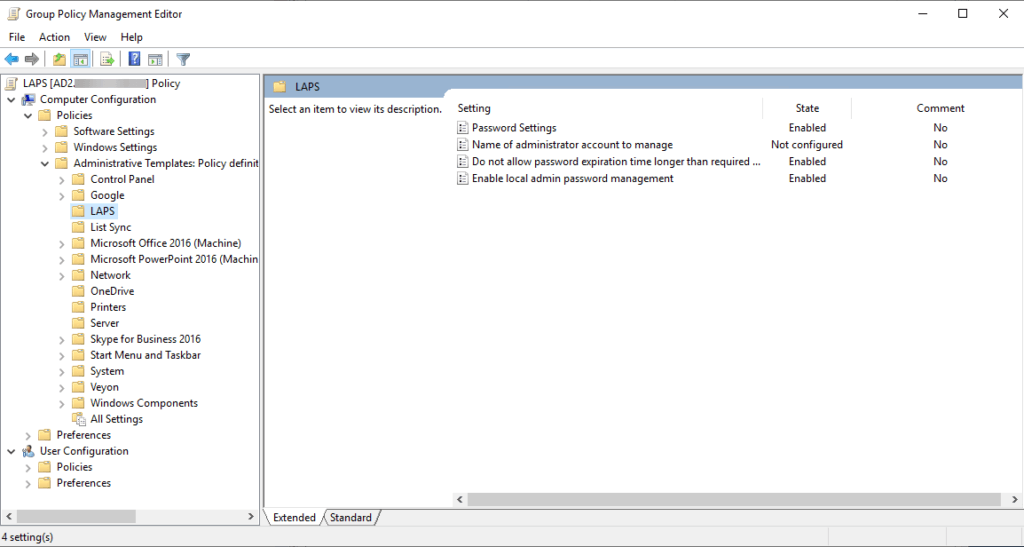
Note if you don’t see LAPS listed you most likely need to copy the admx and adml templates from your local machine to your store.
AdmPwd.admx from %windir%\PolicyDefinitions\ > \domain\SYSVOL\domain\Policies\PolicyDefinitions
AdmPwd.adml from %windir%\PolicyDefinitions\en-US > domain\SYSVOL\domain\Policies\PolicyDefinitions\en-US
Now lets enabled the policy settings. Adjust these that work for your environment
- Password Settings – Enabled
- Name of administrator account to manage – Not Configured (leave this as it will use the local admin account)
- Do no allow password expiration time longer than required by policy – Enabled
- Enable local admin password management – Enabled
Deploy it to your test OU.
Deploy LAPS to clients
There are multiple ways to do this. You can use group policy, SCCM, PDQ, or any other application too. I chose to deploy with PDQ.
Just create a new package, point it to the .msi and your done!
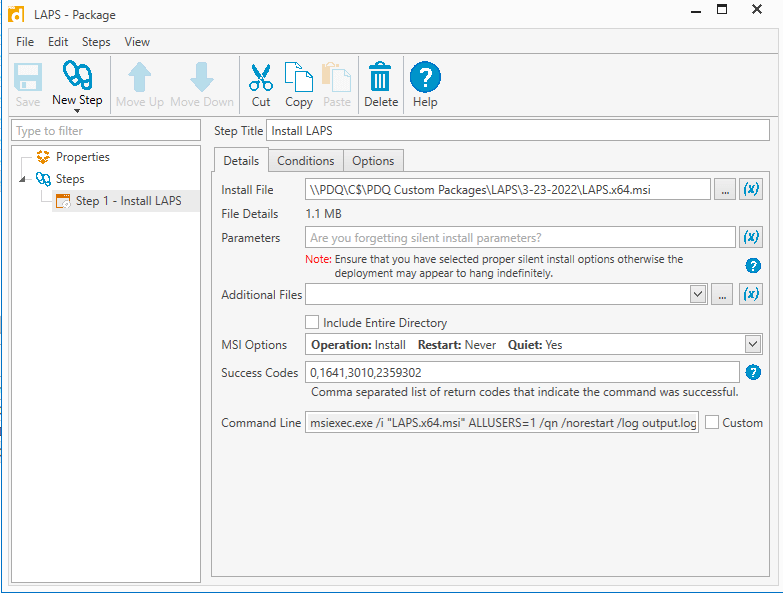
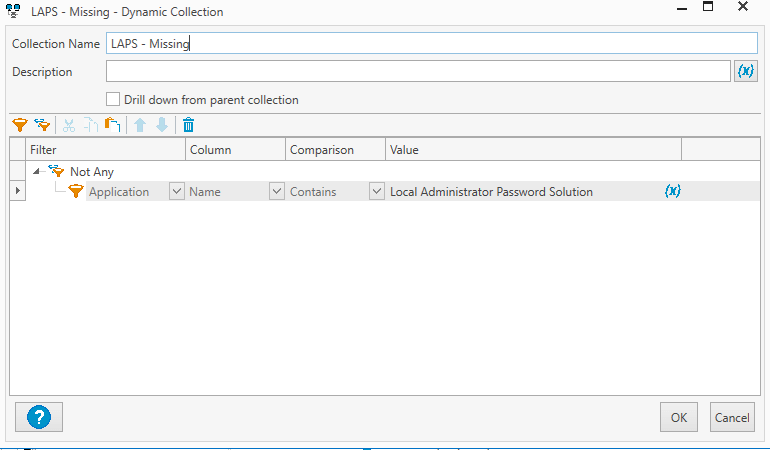
I also created a dynamic group in PDQ Inventory to list all the client machines without LAPS installed. Then deployed my package to it.
- Filter – Not Any
- Filter – Application
- Column – Name
- Comparison – Contains
- Value – Local Administrator Password Solution
Test It
Gpupdate /force on one of your test machines.
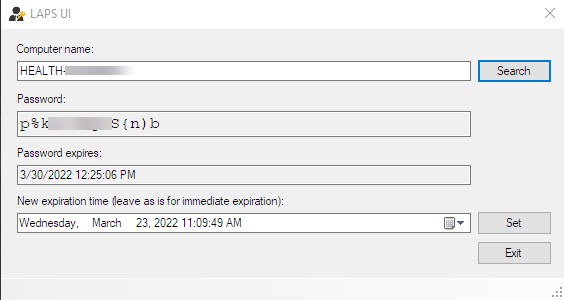
Open up “LAPS UI” and search for your test computer.
If it worked you should be seeing the new password and expiration date.
Once tested deploy it to your organization!
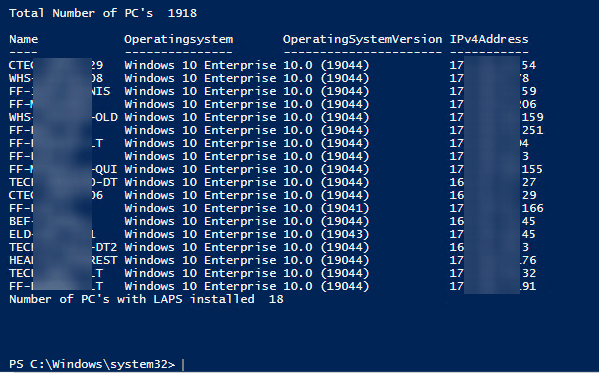
I found this handy script from diychris.com to pull a list of machines that has LAPS by the AD attribute. Open up powershell ISE on your DC and run it:
$computers = Get-ADComputer -Filter 'operatingsystem -notlike "*server*" -and enabled -eq "true"' -Properties Name,Operatingsystem,OperatingSystemVersion,IPv4Address,ms-Mcs-AdmPwd
$lapsinstalledcount = 0
Write-Host "`r`nTotal Number of PC's "$computers.count
foreach ($computer in $computers) {
if(Get-Member -inputobject $computer -name "ms-Mcs-AdmPwd" -MemberType Properties) {
Sort-Object -InputObject $computer -Property Operatingsystem |
Select-Object -Property Name,Operatingsystem,OperatingSystemVersion,IPv4Address
$lapsinstalledcount++
}
}
Write-Host "Number of PC's with LAPS installed " $lapsinstalledcount "`r`n"