I’ve been using the free trial of Netwrix to find failed logins and sadly it’s way out of our budget for K-12 so I’ve been searching for another solution and can help the team. We’ve been having an uptick in AD accounts getting locked due to numerous login failed attempts. 99% of the time it’s from their personal smartphone still having the old password after being required to change it.
Recently built a syslog server using Graylog Open (free) and Ubuntu. It’s a bit of a learning curve (still a ton I don’t know) but I’ve already managed to correct a few issues in our domain with it! It’s super convivence having all your domain controller logs into one easy to search location. Eventually I’ll expand this to our switches and the rest of my servers.
Our setup
Our environment consist of Server 2019 and 2022. Therefore I’ve installed the graylog sidecar installer on each DC and pointed them to the graylog server.
I’m going to assume you already have the inputs setup. So we just need to setup the configuration for the sidecars. Go to System / Sidecars > Sidecars. Click Configuration.
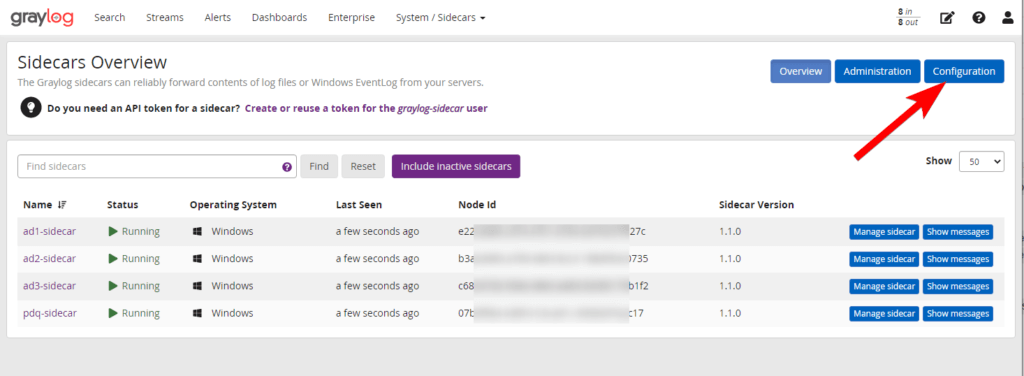
Create a new config and I’m personally going to use winlogbeat collector. The IP should auto fill in the config but just verify before creating.
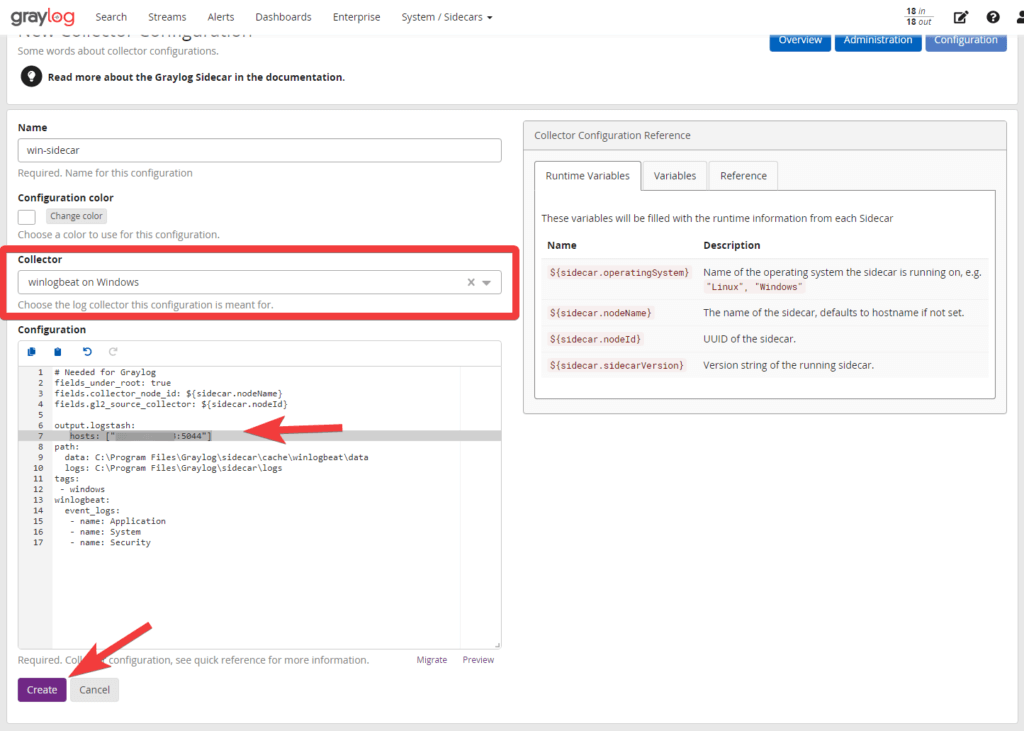
Now if you haven’t done so already install the graylog-sidecar-installer and point it to your graylog server. Once installed you need to install and run the service via cmd (run as admin)
"C:\Program Files\Graylog\sidecar\graylog-sidecar.exe" -service install
"C:\Program Files\Graylog\sidecar\graylog-sidecar.exe" -service start
Once complete go back to the web interface and from the Systems / Sidecars menu select sidecars again. You’ll now see the new sidecars! Let’s push our config by selecting manage sidecar. Select winlogbeat > Configure > Select the sidecar you created. This will push the config to the server. If you were to select show messages you should start seeing your logs flow in.
How to sort by failed login?
Lets do a search for logins. Specify your time frame, I’m doing 30 mins – now. Select your datasource, and your search term: logon.
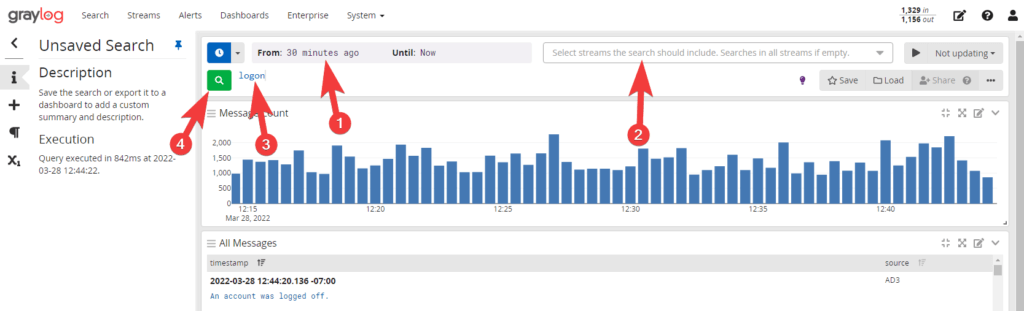
You should now see some messages below. Let break down this data some more and provide easy to read stats. Select one of the event logs that has the information you’re looking for.
Select the fields that would be useful for you to see. For us we want to know how many failed logins, who it was and where. So I’m going to select event outcome then Show top values.
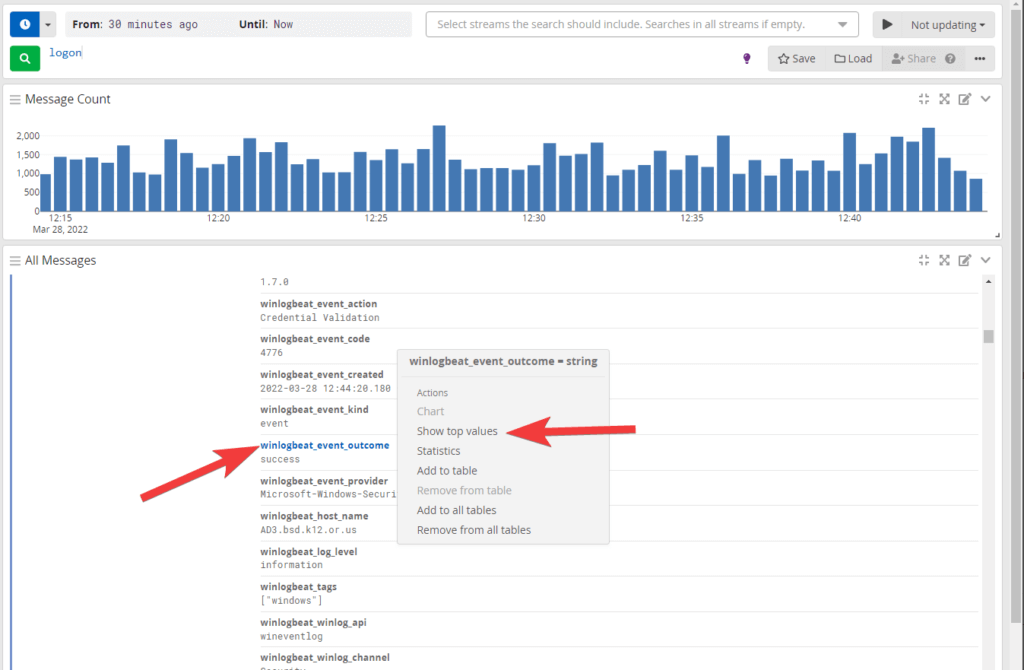
We now have a new chart up top showing the different values and counts!
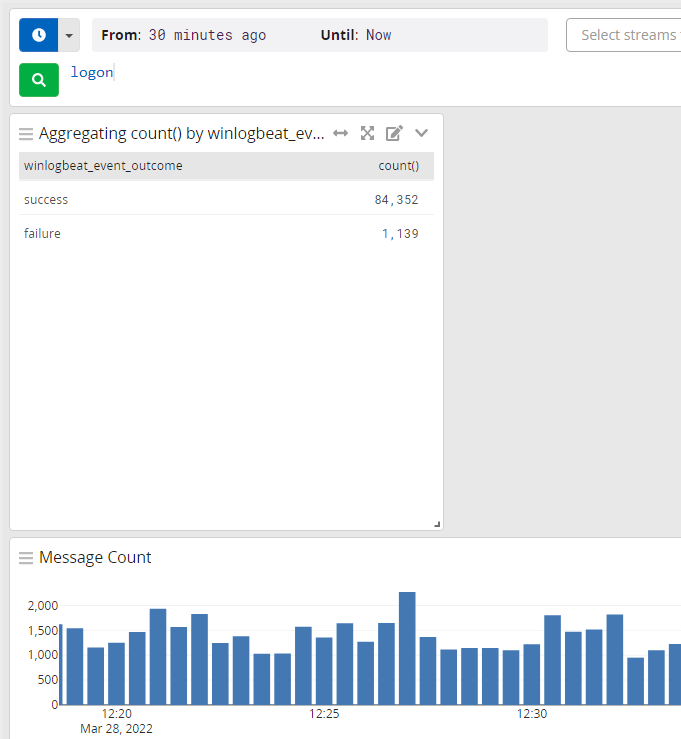
Repeat this process for the rest of the fields you want.
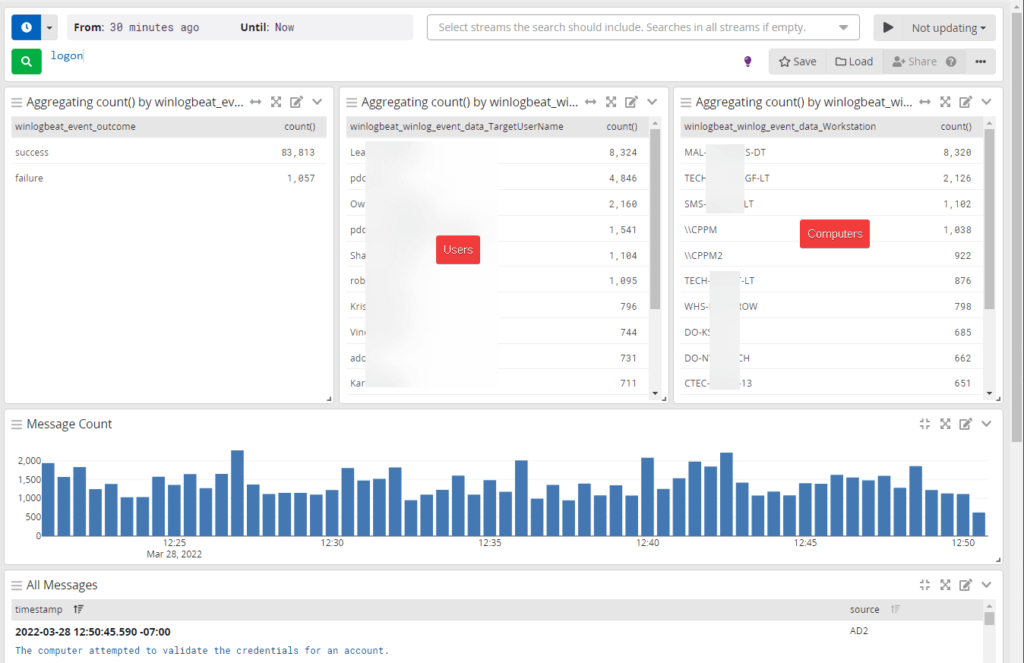
Here’s my new overview which has lots of useful info but it’s still not 100% what I’m looking for. I need to remove the successful logins as I only care about failed at this point.
To remove success click it and select exclude from results.
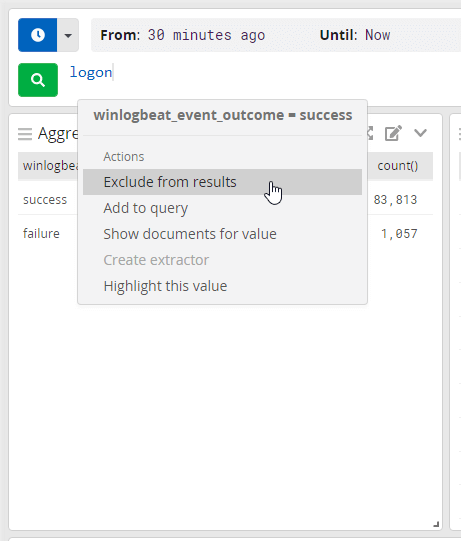
With this new info I can see who exactly is having problems and weather it’s a one off issue or constant by adjusting the time frame.
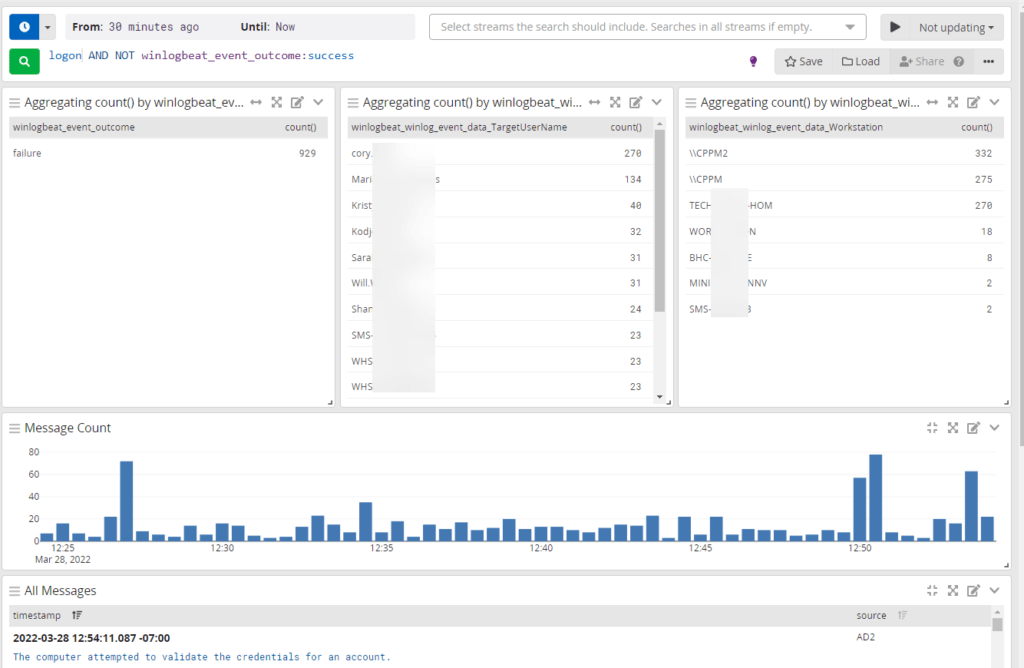
At this point you save this and select one of the users and click add to query to limit your results to that user.
Hope this was helpful!
Hello, Cory!
Here Diego from Brazil. Thanks for your article, It’s just what I was looking, but I have a doubt. With these events in graylog you are able to identify the source of problem? In our case we activated a Windows policy that block the user after 5 logon attempts, but we can’t find the source of the problem. On the Internet we found that might be a lot of problems as mapped drives, windows stored credentials, services running with user accounts. Thanks in advance.
Diego
Hey Diego,
These won’t give you the exact source (such as “Application Name”) but will provide you the source as in the username/device and where that device is trying to authenticate against.
For us, 90% of the time a user has changed their password, which syncs to clearpass (wireless controller) and they don’t update their personal devices such as cell phones. So the device keeps trying to connect and eventually locks them out. With these I logs I can see “username”/device mac address/ip and the source of the authentication such as CPPM in my examples which is our wireless controller. Once I have all that info I can start digging deeper.
If anything, these will give you a great start starting point on where to start digging instead of having to check all your servers. Hope this helps.